Cybersecurity threats are everywhere, and can be especially worrisome for small businesses. Small businesses are often targets of cyber attacks because they have information that is attractive to cybercriminals, without the cybersecurity large businesses and corporations have to keep them safe. When running a business, large or small, you must take all measures to protect sensitive information, your employees, and the technology you use.
4 Tips to Keep Your Business Safe from Cybersecurity Threats
The Cost of Data Leakage
Hackers are attackers outside of an organization who exploit security weaknesses in computer systems or networks to gain unauthorized access to information, cause mischief, or make changes to files, settings, or systems. Hackers have become increasingly sophisticated over the years, and many are experts on a variety of computer systems and software.
With the increase in cyberattacks and data security lapses, many organizations have changed their overall approach to data security and are taking a risk-based approach to data security.
Access Control Best Practices
Audit functions are not only good for troubleshooting a system but also for analyzing logs that can help uncover malicious activity in the form of insider breaches or outsider intrusions. In an investigation, audit logs help verify whether the security policy was adhered to and how an employee may have been involved in a security violation. All root and administrator activities should also be logged, and the size of all logs kept to a manageable size. Actions that should be logged include user-level events, application-level events, and system-level events.
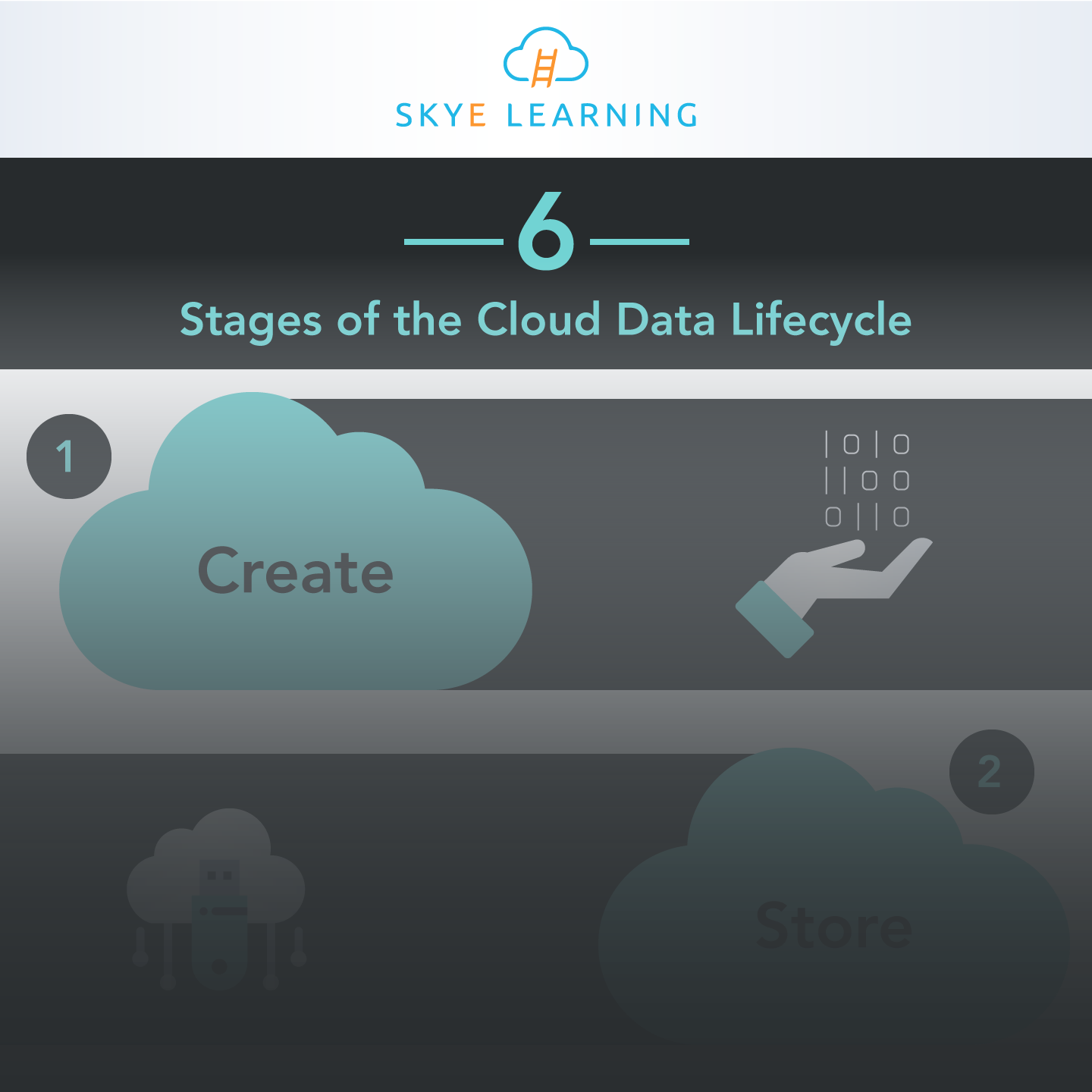
6 Stages of the Cloud Data Lifecycle
The common approach to meeting the challenges of managing data is to map the process of creating and using data to a lifecycle. This is sometimes referred to as data lifecycle management (DLM) or information lifecycle management (ILM).
The purpose of such an approach is to allow an organization to identify the distinct phases data goes through, and then within each step or phase, to identify different security controls that should be in place.
Subject Matter Expert Spotlight: Stephen Palmer
Stephen Palmer is a Lead Business Analyst at MultiPlan and a Certified Business Analysis Professional (CBAP). He has a long career in business analysis and project management. Palmer is a study group facilitator and coach for the Boston chapter of the International Institute of Business Analysis (IIBA). He has also been a panelist at Project Summit & Business Analysis World in Boston, both in 2014 and 2015.
Skye Learning is thrilled to feature Stephen Palmer as a subject matter expert for Skye’s Introduction to Business Analysis course!
Why Data Security is Increasingly Complex
Organizations are increasingly concerned about the loss or theft of electronic information, known as a data breach. Data breaches that result from unauthorized access by individuals within an organization have also become more common. These types of breaches, or data leaks, are commonly called insider threats. Insiders pose a unique challenge because they know how systems are configured, how to defeat these systems, and how to cover up any evidence.
Data Governance
Many people use the terms "data" and "information" interchangeably; however, there is a slight distinction between data governance and information governance. Information governance has more to do with all the processes and systems that gather and use knowledge, enhance it, and share it through the organization. Data governance is a subset of that, and it specifically focuses on the gathering, storing, and usage of data—especially personal data—concerning customers, employees, and partners. This data includes financial information, PII, phone numbers, emails, etc.